The AWS IAM Service the Dwarpal (Gatekeeper) of AWS, Why I am calling IAM Service to Dwarpal ? because Dwarpal is the Protector of your property, he prevent to entered any kind of unauthorised person into your place, he is also destroyer of the Fear of Property Owner , IAM Service doing same thing for your AWS Account, it is the protector of your Organisation and also make you fearless from any kind of unethical activity with your AWS Account, the users within you organisation are only access the stuff for which they are allowed that’s the core concept of AWS IAM Service. In this Article we will deep dive into the how this whole Service is working.
IAM Stands for Identity And Access Management, when you create AWS account root user created by default , but it is good practice that we should not use root account also we should not share root access to anyone instead of we can create separate user (also called IAM user ) with only permissions which are needed to that user.
IAM Users & Group :
Users are the people within your organisation and also can be grouped. users don’t have to belong to a group and user can belong to multiple groups.
Groups only contain users not other groups, we can try to understand this stuffs with some visuals below.
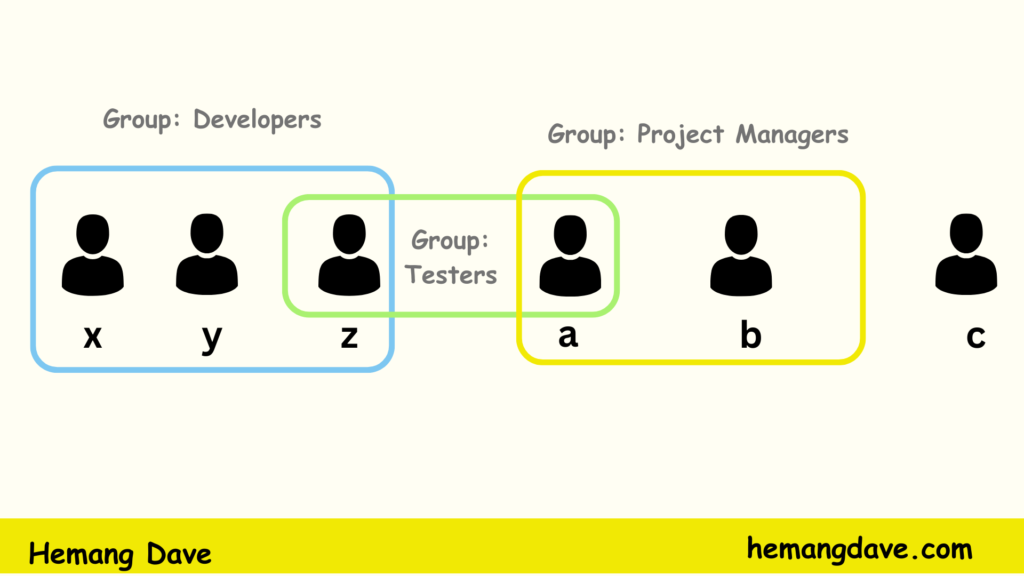
In the above image you can see that there are 3 groups named Developers , Testers and Project Managers (Group names can be anything here we are using some dummy stuff for Example) User X, Y, And z are in the Developers group , User z and a are in the Tester Group and user a and b are in the project managers group and user C is solo. so that’s the beauty of AWS IAM Service.
IAM Permissions
Users or groups can be assigned JSON Documents called Policies. this policies define the permissions of the users or groups.
In the AWS we apply the least privilege principle , don’t give more permission than a user needs.
IAM Polices Structure
{
"Version": "2012-10-17",
"ID":"some dummy id",
"Statement": [
{
"Sid":"some dummy id",
"Effect": "Allow",
"Action": [
"iam:GenerateCredentialReport",
"iam:GenerateServiceLastAccessedDetails",
"iam:Get*",
"iam:List*",
"iam:SimulateCustomPolicy",
"iam:SimulatePrincipalPolicy"
],
"Resource": "*"
}
]
}Let’s discuss each attribute of the IAM Policies which are mentioned above JSON.
Version: policy version of language, always include “2012-10-17”
Id: an Identifier of the policy. (Optional)
Statements: One or more individual statements (Required)
Statement Consists of:
SID: an identifier for the statement (Optional)
Effect: whether the statement allows or denies access.
Principle: account , user, role to which this policy applied to.
Actions: list of actions this policy allows or denies
Resource: List of resources to which actions applied to.
Condition: conditions for when this policy is in effect. (Optional)
IAM – Password Policy
Strong Password = Higher Security for your Account
In the AWS you can allow set of a password policy
- Set a minimum password length.
- Required specific character types.
- Include uppercase letters.
- include lowercase letters.
- Numbers.
- Non-alphanumeric characters.
- Allow all IAM users to change them own password.
- we can set Require users to change their password after some time – password expiration.
- Prevent Users to re-use password.
That’s all for this Article , IAM service has more precious features, Like MFA, IAM Roles etc, we will cover all these features in further Articles with Practical Guide.
Subscribe to our email newsletter to get the latest posts delivered right to your email.


Comments